Using An OpenWRT One to Extend a Network to a Remote Location
First, why this project? The place that has become to be known as the compound is essentially our cottage, or home away from home. We have our own little basement apartment and love to get away from the city to spend some time there. We have two sources of internet there. We have Starlink, which was brought over from my parent's old place and I decided to get a home 5G connection, to see what it is like. I am hoping to use this as a stable backup for a site-to-site connection for two main reasons. One would be a site-to-site connection for media and whatever, one a network scale instead of an individual device. Two would be sending information from sensors and/or IoT devices back to the main servers for processing (future project).
The OpenWRT One
As someone who loves DD-WRT and has never used OpenWRT, one day shopping on AliExpress for watch parts I came across the OpenWRT One. I instantly was sold once I read that is was a collaboration between BananaPi and OpenWRT. Though, I have never used either of the products, from what I knew of them, this seemed to be a product I was willing to support (I hope I am not wrong about that). So, I bought it.
What Am I Working With?
The network is already designed to take Wireguard connections at home. I have incoming Wireguard connections terminate at a pfSense firewall and are given specific access depending on the incoming client.
The goal is to have this network treated in a similar fashion. Most of the clients are not given access to the servers themselves, but, are provided with a specific DNS server to connect to and one or two proxies to redirect the approved traffic. This will be given to all the clients of the compound site.
Let's Get Started

I opened the box to the new toy and - as usual - started running into the typical technical hurdles:
- Went to connect to WiFi; Oh, it's disabled by default
- Went to connect via ethernet; Oh, my laptop doesn't have an ethernet adapter
- Finally, connected! Let's update the firmware; What do you mean this version doesn't have the UI installed
- Now how do I change the IP addresses...
Anyways, after a silly amount of time and lessons learned, we are at a spot where we have a device to configure.
The default LAN IP Address is the infamous 192.168.1.1. Let's SSH into the box and get that changed:
uci set network.lan.ipaddr='192.168.100.1
uci commit network
/etc/init.d/network restart
I restarted the unit to receive a new IP address.
Next step is to install the required packages for Wireguard (References to Luci are the packages for the UI).
apk update
apk upgrade
apk add luci wireguard-tools luci-proto-wireguard
Now, I will reboot again (or you can restart the services).
At this point let's generate the public and private key pair.
wg genkey | tee wg.key | wg pubkey > wg.pub
This will produce a public key and private key, placing them in the corresponding files wg.key and wg.pub. We will need these for the configuration on the server and this, the client. Now, take the keys and some other parameters then place them in environment variables, so we do not store these in plain text anywhere on the machine; we will delete the files after.
NOTE: Make sure you obtain the peer public key as well. I have placed that in wg-peer.pub. This will be used for the peer connection.
NOTE 2: All this can be done via the CLI - awesome - I just decided to do a more visual approach since I was learning the UI, CLI and OpenWRT in general!
Poking Through The UI To Get This Done
Again, we will be going through the UI as examples, this can all be done easily with the command line and uci.
I did not go through the details of the menu, so you may have to do some hunting. I went more specific into the configuration piece.
So, start by hunting down the interface page and adding a new interface. Set the interface to the Wireguard VPN type which will now be there; it wouldn't have been there before. Once it has been added you will be brought to the next page, shown below.
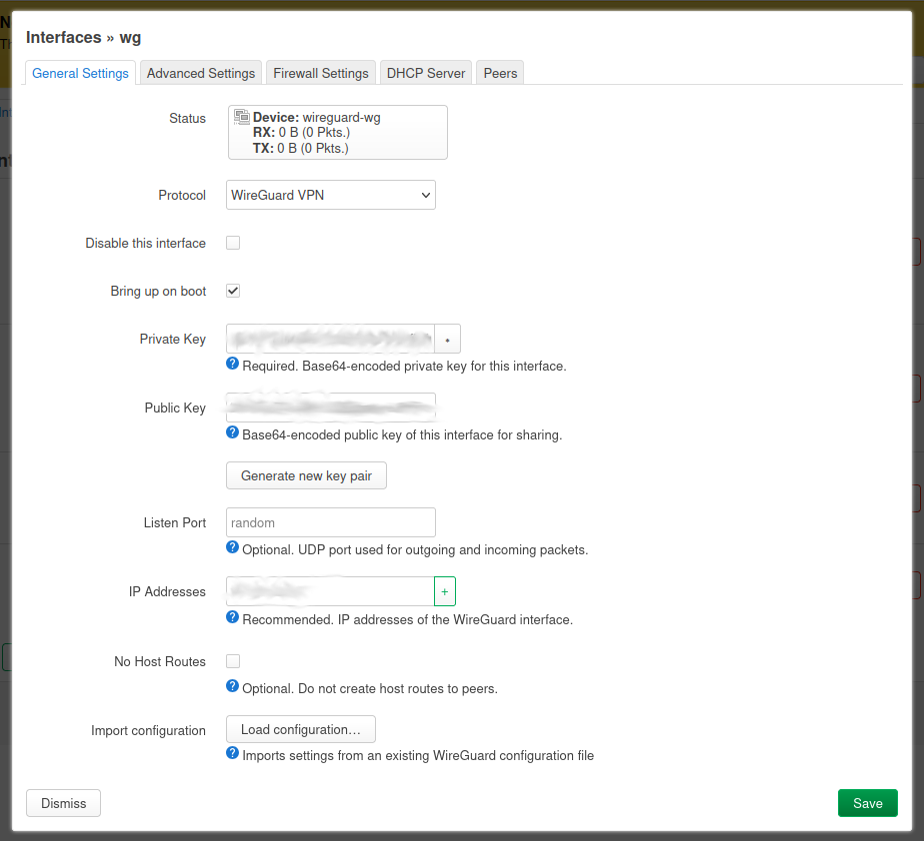
This is where we insert the information on the local machine, aka the OpenWRT One. The information to be filled in is the private key, public key and IP Address. The public and private keys were the ones generated earlier. After that we move to the Advanced Settings tab.
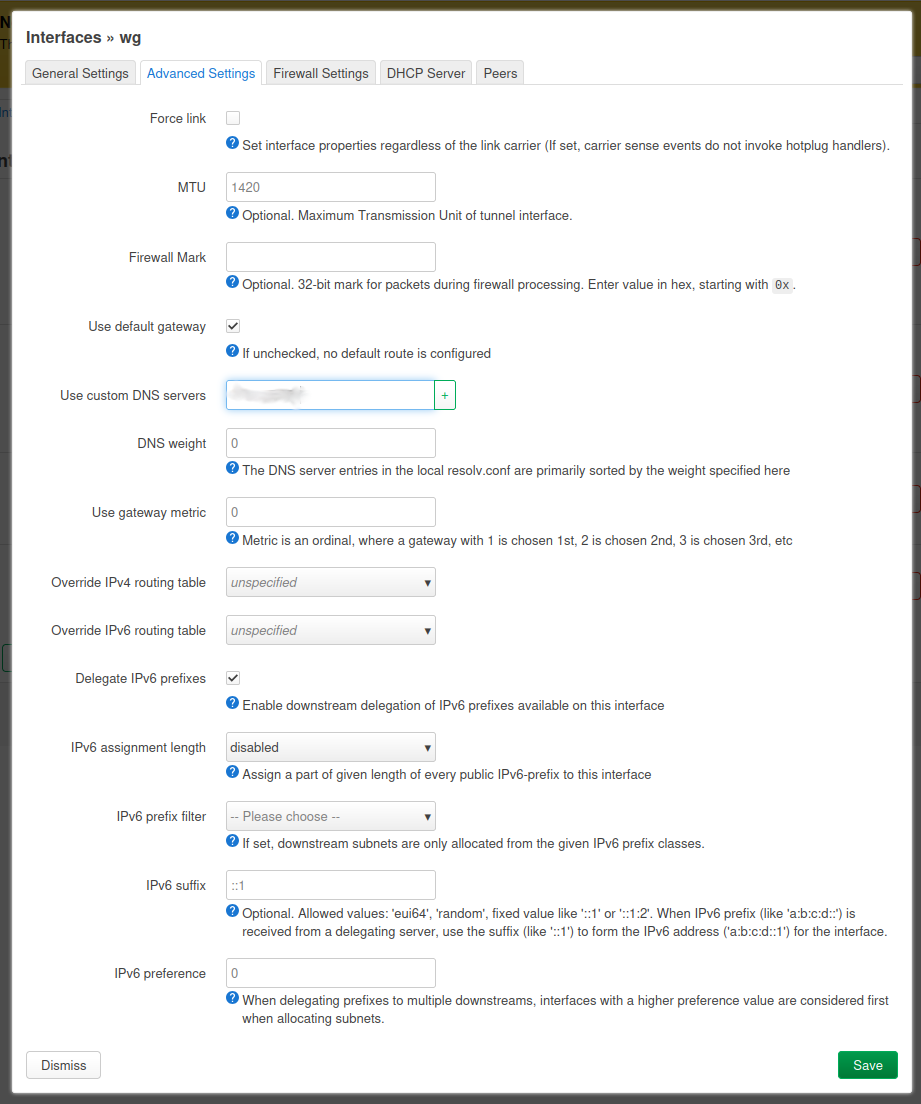
This is where we can set the custom DNS server (read the caveats section!) as well as disabled the IPv6 assignment; which I am currently not looking to utilize. After that, move to the Firewall Settings.
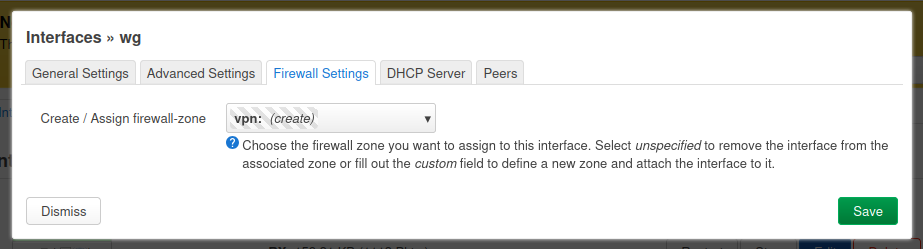
Here we are simply creating a new zone called "vpn". We are skipping the DHCP Server tab and moving to the Peers tab.
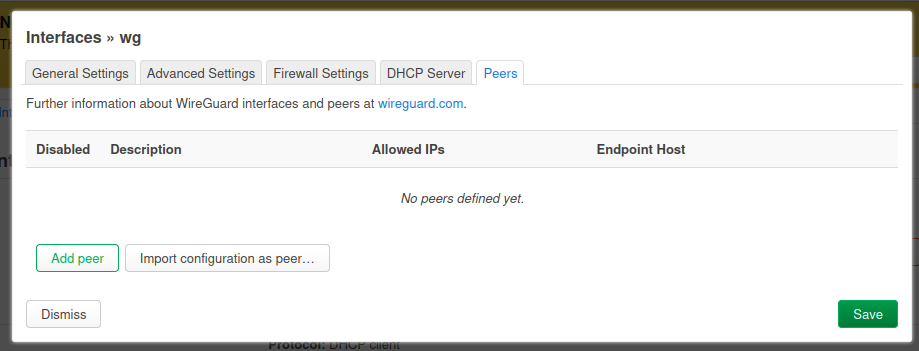
This is the last tab and where we will be setting up the "peer" or the "home network".
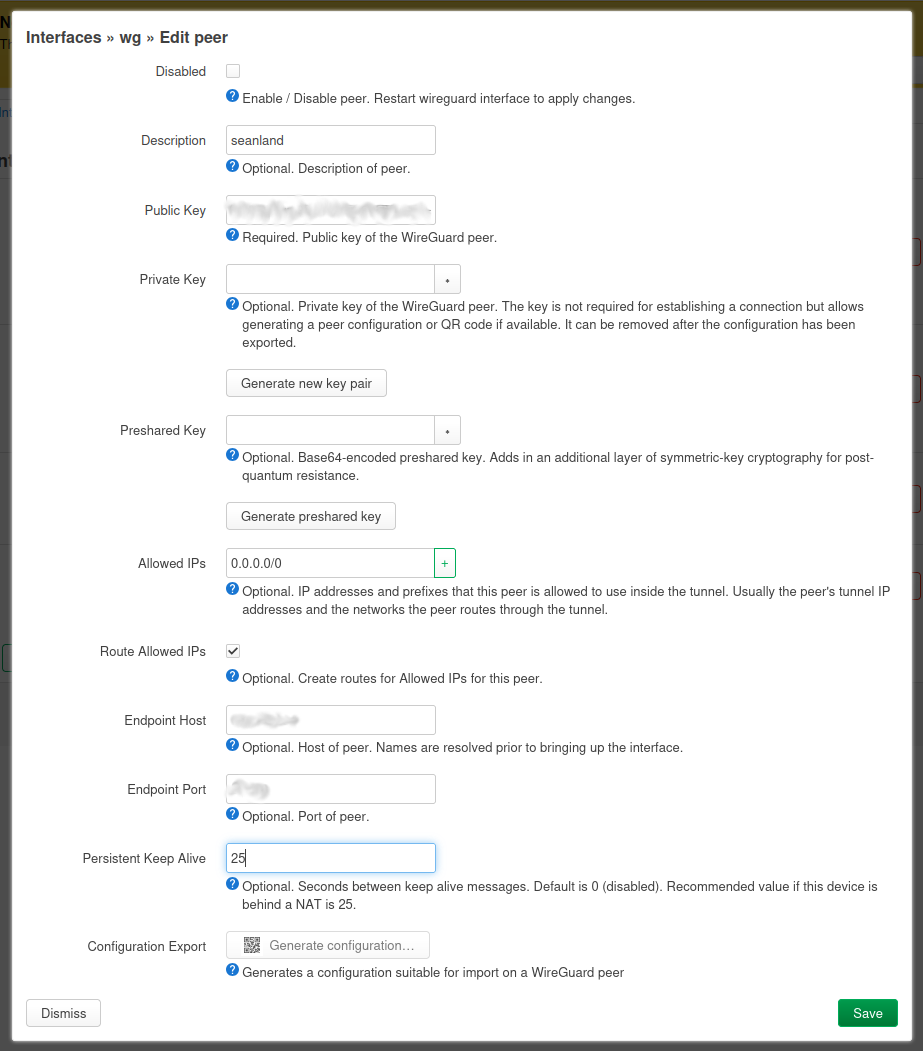
This is where we configure the destination. The key things to fill out:
- The public key: This is the peer public key. The one you got from the other end of the connection
- Description: Yeah, call it something.
- Allowed IPs: This is where we want to set 0.0.0.0/0. This will route all IPs to this peer.
- Endpoint Host: The domain or IP address of the peer.
- Endpoint Port: The port the connection will be created on.
- Persistent Keep Alive: Set this to 25.
Now save this peer. Lastly, we want to head to the Firewall Zones and configure the VPN firewalls.
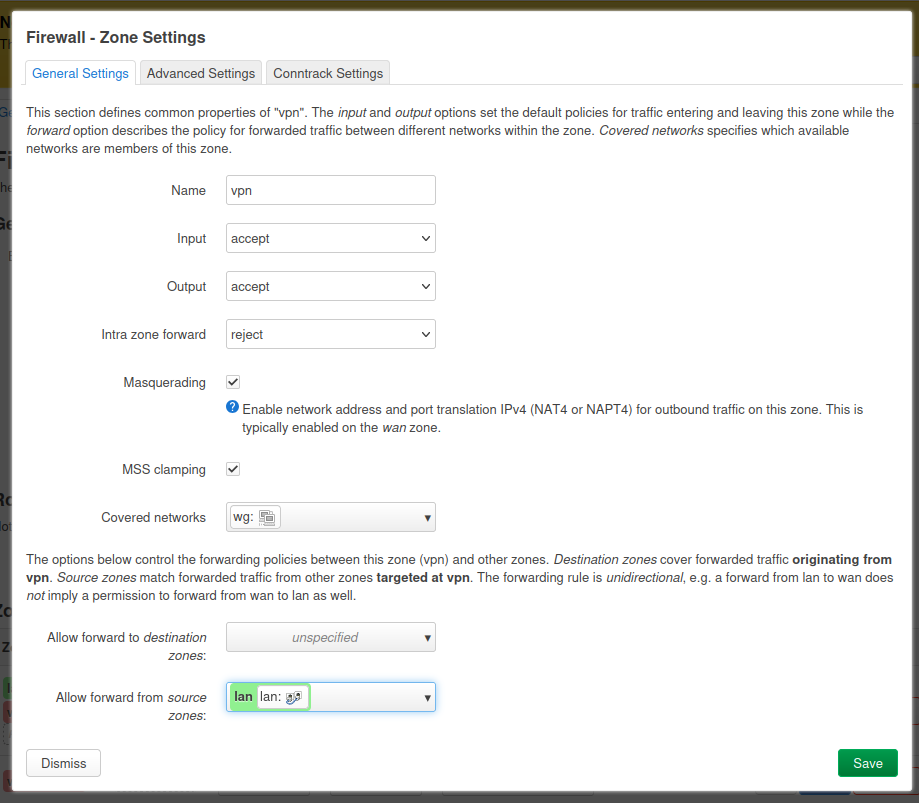
Simply, this configuration - as shown above - is to allow the lan traffic to go through the wg network.
After this point, one last restart should have you on the way!
Caveats With This Setup!
Two big things I want to point out:
- The DNS will be leaking like a firehose.
- There is definitely more firewall finetuning that can take place.
The DNS situation is tricky, as we want it to be established "PostUp" of the interface. In WireGuard, I can simply add a one-liner that modifies to an internal (DNS from the peer.) DNS server. I attempted to use a hotplug script on OpenWRT, but, it would break the VPN tunnel upon restart (from what I can tell). The domain (the peer is a domain) would pull a local IP and not work. This is probably the method I have to take, but, I need to do some more testing. For now, I have gotten around it by defining the DNS on the machine itself. Fortunately, I do not have a large number of machines connecting to that network, especially now and the connection is going to be a permanent full tunnel; so, little hassle.
The security aspect, though there are not a lot of risk with how it is. I could tweak the actual rules beyond the zones. I do have a number of proxies and a firewall beyond this peer, so there are additional mitigating factors. A few other things I will do in the future, is remove the UI and simply do all the commands via SSH. After that, I will just lock the unit down in terms of access both to the box and for the traffic.
Takeaways
This is my first time using OpenWRT and WireGuard to establish a tunnel from one site to another for personal use. I am excited to be able to utilize that network, just like I am at home. I will also have network services running at the compound just like home IE. Media and even better, the PiHole. The latency and performance decrease over the VPN should be negligable or absolutely minimal. Worst case, after all of this, I have also built a portable firewall and router. This is a great little project for anyone that wants to travel for work and pleasure. It is configured in a such a way that it should be easily transplanted anywhere you go (unless set location blocks the traffic).
I hope this was helpful for anyone else looking to do something similar. It is fairly simple to get up and running. Good Luck!
